Be CyberSmart!
Make Cybersecurity a priority every day. Advice from staysafeonline.com: Keep cybersecurity at the forefront of your mind as you connect daily. Before purchasing a device or online product, do your research. When you set up a new device or app, consider your security and privacy settings and update default passwords. Cybersecurity should not be an afterthought.
Learn more about Cybersecurity and staying safe online:
Password Security
Make passwords long and strong
Combine capital and lowercase letters with numbers and special characters to create a more secure password. Change any default passwords on your mobile device to ones that would be difficult for someone to guess.
What makes a Good Password?
To start, your password should be at least 10 characters long, with at least one capital letter, one number, and one special character (“@”, or “%”, etc…).
As an added layer of security, change your passwords on a regular basis to ensure that you stay ahead of the hackers.
| Bad | Better | Excellent |
|---|---|---|
| cynthia | Cynthia1970! | Cynth!@197o! |
| cynthiasmith | CynthiaSm!th1970 | Cynth!@Sm!th197o |
| Buster! | Bu$t3r2022 | Bu$t3r!sBr0wn |
It’s important to remember that you should not use the same password for multiple accounts – no matter how strong it is – because if one account gets compromised, then they’re all compromised.
Unique account, unique password: Use different passwords for different programs and devices to thwart cybercriminals. Do not choose options that allow your device to remember your passwords.
Use a Password Manager
Everyone can forget a password. Use a password manager tool (i.e…lastpass.com) to help organize your passwords.
Get Two Steps Ahead
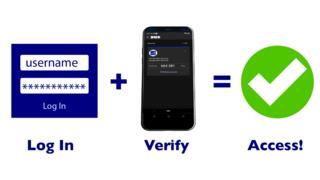
Turn on two-factor authentication or multi-factor authentication– on accounts where available. Multi-factor authentication can use anything from a text message to your phone to a token to a biometric like your fingerprint to provide enhanced account security.
Phishing
What is Phishing? Phishing is an attempt by an individual or group to solicit personal information from unsuspecting users by employing social engineering techniques. Phishing emails are crafted to appear as if they have been sent from a legitimate organization or known individual. These emails often attempt to entice users to click on a link that will take the user to a fraudulent website that appears legitimate. The user then may be asked to provide personal information, such as account usernames and passwords, that can further expose them to future compromises. Additionally, these fraudulent websites may contain malicious code.
Think before you click! Review the signs of Phishing below:
- Urgency: Urges you to act quickly because your account may be suspended or closed.
- Generic Greeting: Doesn’t address you by name, but uses a generic greeting like “Dear valued customer.”
- Validate or Update Information: Asks for account numbers, passwords or other personal information.
- Includes Errors: Contains misspellings or grammatical errors.
- Unusual Content: Is from someone you know, but includes a strange subject line or unusual attachments.
- Unknown Link: Contains links to unknown or suspicious websites.
- Plausible Sender: Claim to be from your military service, government organization, Internet service provider or bank.
- Fake Website: Direct you to a Website that looks real.

Multifactor authentication (MFA) is a security technology that requires multiple methods of authentication from independent categories of credentials to verify a user's identity for a login or other transaction. Multifactor authentication combines two or more independent credentials: what the user knows, such as a password; what the user has, such as a security token; and what the user is, by using biometric verification methods.
The goal of MFA is to create a layered defense that makes it more difficult for an unauthorized person to access a target, such as a physical location, computing device, network or database. If one factor is compromised or broken, the attacker still has at least one or more barriers to breach before successfully breaking into the target.
Secure shell endpoint access streaming prevention to detect attacks in progress online and offline attack prevention. At the core of Carbon Black’s endpoint security software is CB Defense. CB Defense serves as a next-gen antivirus (NGAV) as well as an endpoint detection and response (EDR) solution. Audit and remediation - real-time device assessment and remediation - Easily audit the current system state to track and harden the security posture of all protected devices.

